
This article was created in collaboration with SecureStack and is part of the Stone & Chalk Masterclass series. You can watch the full masterclass here.
For startups, the onus is often on the founders to focus on the security of data and intellectual property from the get go. If you’ve just started out, building security into your system from day one can help minimise cost in the long run and reduce the likelihood of malicious attacks. If you’re looking to implement security measures after the fact, it's never too late to start.
“Understand that every time you add a security measure, every time you have that success that makes the company better that makes your platform and your product better.” – Paul McCarty, SecureStack CEO.
Why cyber security is important to your startup
Building security into your tech stack from the start is a no-brainer, but it’s often overlooked until it’s almost too late. Through a masterclass, SecureStack CEO, Paul McCarty, helps us shed light on the importance of an early focus on security, “If you wait until you release something to implement security procedures, then it's going to cost you 150 times more than if you addressed it early in the process.”
Not only does security protect your intellectual property and enhance your company assets, it also facilitates connections with other organisations. The term “security stack” is used to describe the myriad of cyber security tools startups can use to protect themselves from cyber threats – typically including traditional antivirus software and firewalls as well as more complex tools like DNS filters. The layers of tools make up a stack, and these all aim at heightening the security of your product and mitigating its vulnerabilities.
Cyber security also has a profound impact on your growth opportunities. Government connections, partnerships, investment and cooperation you can attract, not to mention the trust of your consumers, are all directly affected by the stability and effectiveness of your cyber security protocols.
5 common misconceptions founders have about cyber security
1. Software engineers are security experts
Many founders assume that their software developers are also security experts. In reality, most of them aren’t. This assumption that someone else is taking care of security when they’re not impacts the startup sector more than anything else. Unfortunately, most startups value speed and efficiency over cyber safety. “We incentivise developers, software engineers to do things as quickly as possible to deliver features. We are not incentivising those engineers to deliver things securely,” Paul said.
The push for efficiency has led to 48% of software developers admitting to knowingly pushing vulnerable code in their development activities and 70% of developers admitting to skipping security measures entirely due to time pressure. But that's exactly the kind of pressure our software engineers are facing. In order to break this cycle and build a greater focus on security from ground zero, founders have to be an active participant in the security process and hold developers accountable for building a secure product.
2. CEOs don’t need to know the ins and outs of security
It’s a common assumption that the CEOs, or founders of a company, don't need to know how the sausage is made. This can’t be further from the truth.
The applications we’re building now are more complex than ever before, and most are using new languages and frameworks. Further, the security challenge has now moved to the user’s browser, and everything that goes into your apps – payment processor, analytics engines, source codes – all have their own security challenges and are targets for malicious activities.
So why is this your problem as a founder?
As a startup, you probably don't have any security experts on your team, but you still need someone to keep tabs on the layers of security and hold others accountable for delivering products that are cyber secure by design. If you don’t have in-house security experts, then that person should be you.
3. Free tools are good enough
This may be true in 2001 but not today. Threat actors have upped their game. You need to invest in security, even if you're trying to be cost effective. You need to spend money on it just like you're spending money on insurance for your business.
There’s a misconception that security is costly. In reality, some of the things that you need are not that expensive. There are two ways that you can pay for security: paying for premium tools or hiring people to develop or implement free tools. Either way, you need to set aside an outlay.
4. Cloud providers have everything under control
Too often, founders assume that platforms credible cloud service providers have the capability to secure their products, but this isn’t always the case. Cloud security is a shared responsibility model. This model demonstrates that cloud providers only share a certain amount of responsibility, while you own the rest. Cloud services also have their own security challenges, and that's something you need to take into account.
5. A penetration test is enough
There's so much more to application security than just a pen test. There are multiple stages of how you build software, called the software development lifecycle or the DevOps lifecycle.
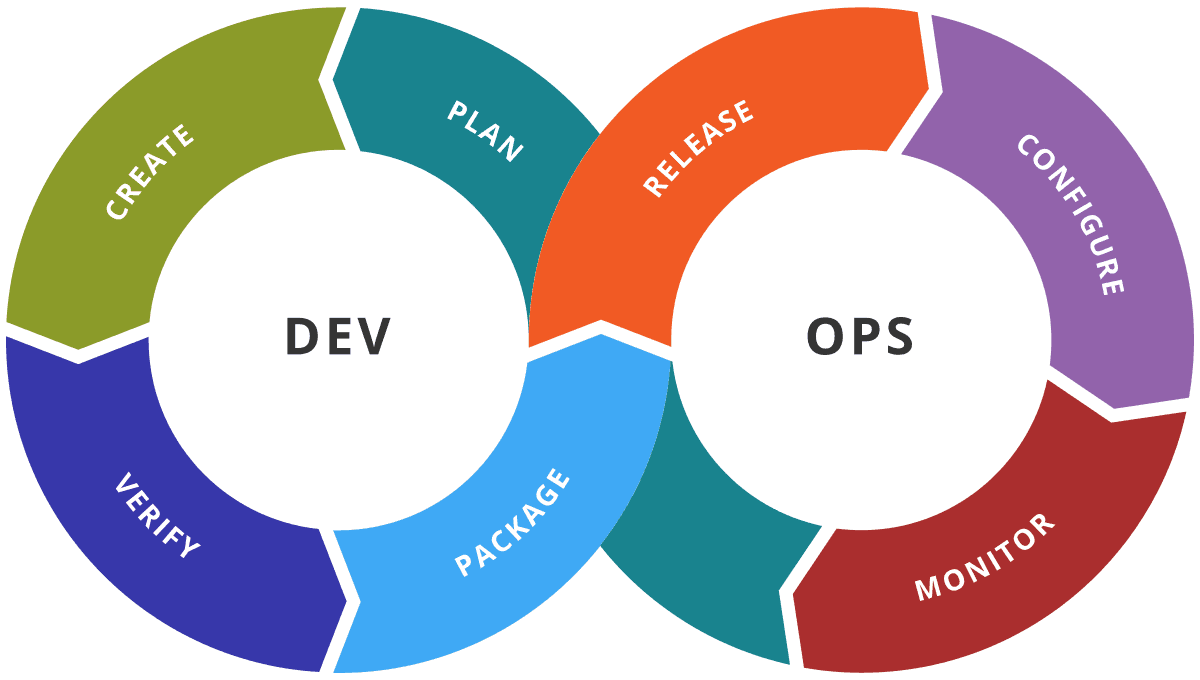
This lifecycle demonstrates an infinite loop of software development – where engineers write the code – followed by testing – where you make sure that it does what it's supposed to – followed by the release and other stages.
This is a complicated process and a pen test only works at the very end of it. So pen testing is only one small thing you can do, but it’s also expensive and may only be done once a year. There's a lot more to application security and doing things the right way than a pen test.
7 things you should secure right now
All things considered, below are seven things you should spend time securing today as the first step towards building a more secure product for your customers.
1. Your devices
The simple adoption of endpoint detection and response (EDR) is a quick and easy method to stop malicious actions on your devices. It should be adopted as best practice by any company with laptops or computers in use.
Remember to backup your devices. Backups are cheap and easy. They can run when you’re not using your computer, so you should already be doing it.
As a startup, you should also avoid outsourcing software development offshore, which poses a risk wherein your intellectual property will remain in a foreign device located in a different country even after the contract is terminated. Furthermore, you don’t have any control over what secure methods they’re using to access your important resources.
2. Software your team writes
Gain access to your application source code – your intellectual crown jewels – if you haven’t already. Then, look at enabling logging and backing it up. Centralised logging will allow your team to identify issues and solve problems much faster by having all historical data at their fingertips.
In addition, you should ensure all credentials and private keys are stored securely in a vault and not in a file that gets added to the source code. Below are several more ways developers can tighten the security of their applications:
- Encryption: All data should be encrypted in transit and at rest. This includes database storage, file storage, sessions and cookies.
- Password hashing: Passwords should not be stored in plain text but should be hashed to protect user information.
- Application whitelisting: Applications should be accessed only by the minimum resources needed to complete a task. This limits the vulnerability of each application.
- Sufficient logging: The software must have sufficient logging capabilities. This allows the developer to clearly and quickly identify problems.
3. Third-party libraries and frameworks
More than 90% of the code inside your application may have been pulled in via third-party or open-source libraries. While this is standard practice and the majority of these libraries are perfectly fine, you still need security measures in place.
Ensure your developers take time to vet third-party libraries and frameworks before introducing them into your source code. Consider engaging a managed security service provider (MSSP) for added safety. MSSPs specialise in offering security as a service and can help monitor your networks for suspicious activity and unauthorised access. For a startup operating on a lean budget, they give you the ability to bring in a security expert without having to pay for a full-time role.
4. Cloud resources
Cloud security is the protection of any data stored within the cloud from potential threats. The public cloud isn’t secure by design; it can be but rarely implemented that way. Even when implemented securely, it’s still up to your team to scale it.
Update the underscoring infrastructure constantly as the application changes and so does the source code, especially if you create new features, test and push them out to customers on a regular basis.
5. Continuous integration and deployment (CI/CD) process
Many startups spend months or years building out a CI/CD pipeline that works. Retrofitting security after the fact would naturally invite a lot of resistance. The answer for this is to build security into the process from the beginning. Source code analysis, security testing and runtime security are all measures that can keep your CI/CD process secure.
However, if you’ve already built out your pipeline, know that it’s never too late to incorporate security into the process. Reach out to an expert – or an MSSP – for guidance. Either way, you need that security to test and make sure what you’re deploying is good for your customers.
6. Web vulnerabilities
Web vulnerability assessment is of utmost importance as most modern web apps run on customers’ devices, so a lot of attacks happen on the user’s browser. Unfortunately, you just don’t have the same visibility going through the cloud resources as you would have through the older kind of data centre model.
There are many tools out there you can use to assess your web vulnerabilities. The caveat is that some of them may overestimate your capabilities and give you a false sense of security. Do your due diligence, seek expert advice or conduct some research online before deciding what tool works best for you. In a nutshell, what you need as a founder is visibility into what you’re building for your customers.
7. Assets
Public assets include the data, people, devices, systems and facilities that enable your startup to achieve business purposes. Startups tend to have more assets than they realise as developers often spin up temporary resources that can stick around forever. It’s important to keep track of these assets because each one is a potential target. If you don’t know what you have, you won’t be looking to see if they’re under attack.
To summarise, it’s easier, cheaper and faster to build security into your startup early on; but it’s never too late to start building a more secure product. For support on how to achieve that, reach out to the experts at SecureStack.